Below, we're collating the best Black Friday sales we could find on SDR and related products.
If you find any other good sales for SDR or related products, please post in the comments!
RTL-SDR Blog
We're currently offering $5 of V3 dongles (including the V3c) on Amazon. The sale will last until Monday 1 December, and only while stocks last.
RTL-SDR Blog V3 Dongle + Antenna Kit: US$47.95 US$42.95 (Link)
RTL-SDR Blog V3 Dongle Only: US$37.95 US$32.95 (Link)
RTL-SDR Blog V3c Dongle Only: US$39.95 US$34.95 (Link)
We also want to add that in December, the price of V4 dongles will be raised, due to rising chip costs, and dwindling R828D stockpiles, so buying now is purchasing while essentially on sale.
We're also participating in the Airspy 25% sale with the YouLoop listing on our store. The sale takes the price down from $39.95 to $29.96.
Airspy
Airspy offers low-cost RX-only SDRs. Airspy is holding a 25% off Black Friday sale. Black Friday is usually their biggest discount of the year. The sale is offered by their official iTead store and by most resellers. Links to their sales are platforms available here https://airspy.com/purchase
Airspy R2: US$169.00 $126.75
Airspy Mini: US$99.00 US$74.25
Airspy HF+ Discovery: US$169.00 US$126.75
Airspy SpyVerter R2: US$49.00 US$36.75

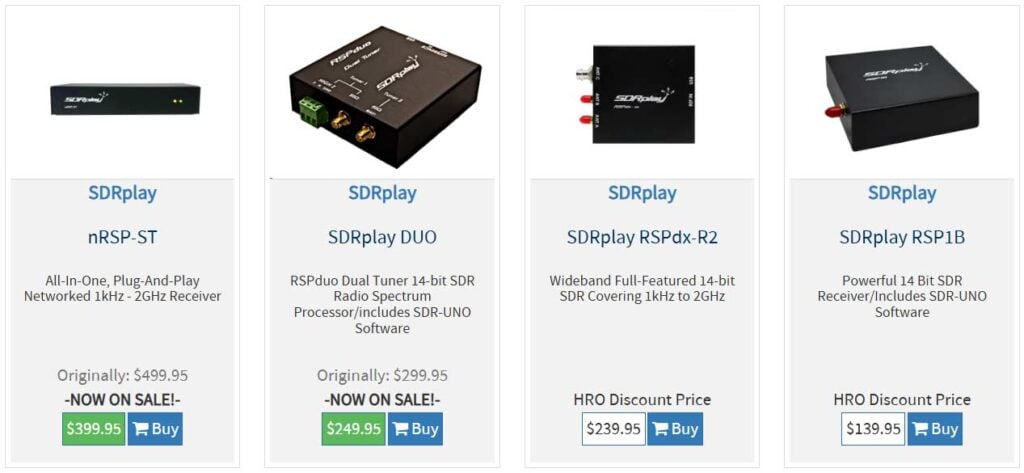
SDRPlay
SDRplay offers low-cost RX-only SDRs. There do not appear to be any direct Black Friday deals from SDRplay, but on Ham Radio Outlet, the SDRplay nRSP-ST and DUO units are on sale. The RSPdx-R2 and RSP1B appear not to be on sale.
SDRplay nRSP-ST: $499.95 $399.95
SDRplay DUO: $299.95 $249.95
FlexRadio
FlexRadio offers high-end SDRs aimed at ham radio users. They are currently running a Black Friday deal as shown in the screenshot. https://www.flexradio.com/products/categories/black-friday/

Ham Radio Prep Course
While not physical SDRs, some people interested in getting their amateur radio licence in the US may be interested in this study course, which is discounted for Black Friday. https://hamradioprep.com/black-friday
They have various course bundles on sale, but this screenshot is of the full bundle.